Interfaces That Provide An Avenue For Exploits . on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. Apis provide a digital interface. another common security vulnerability is unsecured application programming interfaces (apis). In this article, we will.
from www.slideshare.net
another common security vulnerability is unsecured application programming interfaces (apis). while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. In this article, we will. in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. Apis provide a digital interface.
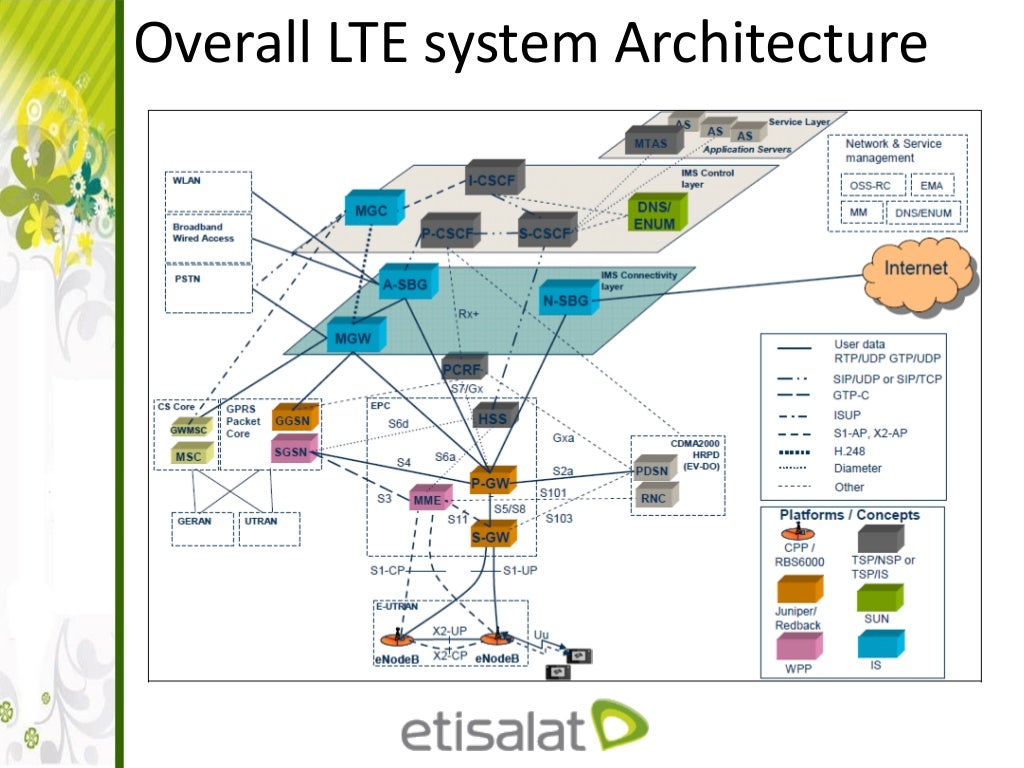
LTE Architecture and interfaces
Interfaces That Provide An Avenue For Exploits in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. In this article, we will. Apis provide a digital interface. while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. another common security vulnerability is unsecured application programming interfaces (apis).
From slideplayer.com
Prof. Thomas Sterling Department of Computer Science ppt download Interfaces That Provide An Avenue For Exploits another common security vulnerability is unsecured application programming interfaces (apis). while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. In this article, we will. Apis provide a digital interface. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks. Interfaces That Provide An Avenue For Exploits.
From www.codexploitcybersecurity.com
Sophos XG Firewall The Complete Build and Maintenance Guide Basic Interfaces That Provide An Avenue For Exploits while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. Apis provide a digital interface. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can.. Interfaces That Provide An Avenue For Exploits.
From www.h2020-dragon.eu
Structure Dragon Project Interfaces That Provide An Avenue For Exploits Apis provide a digital interface. another common security vulnerability is unsecured application programming interfaces (apis). attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. In this article, we will. while apis bring. Interfaces That Provide An Avenue For Exploits.
From h0mbre.github.io
HEVD Exploits Windows 7 x86 UseAfterFree The Human Machine Interface Interfaces That Provide An Avenue For Exploits while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. another common security vulnerability is unsecured application programming interfaces (apis). in the context of penetration testing, a pentester may use file inclusion exploits to. Interfaces That Provide An Avenue For Exploits.
From slideplayer.com
Sessions 43 & 44 Accessing data using a common interface OGSADAI Interfaces That Provide An Avenue For Exploits Apis provide a digital interface. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. In this article, we will. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. another common security vulnerability is unsecured application programming interfaces (apis). in the context. Interfaces That Provide An Avenue For Exploits.
From www.researchgate.net
Examples of CCD methods exploiting multiple interfaces Download Interfaces That Provide An Avenue For Exploits attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. Apis provide a digital interface. while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. another common security vulnerability is unsecured application programming interfaces (apis). in the context of penetration testing, a pentester may. Interfaces That Provide An Avenue For Exploits.
From slideplayer.com
Interfaces 101 Interfaces provide connectivity for the drawers to Interfaces That Provide An Avenue For Exploits Apis provide a digital interface. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. In this article, we will. another common security vulnerability is unsecured application programming interfaces (apis). in the context. Interfaces That Provide An Avenue For Exploits.
From onehack.us
AutoXploit Auto Payload Generator & Exploiter Tools & Scripts Interfaces That Provide An Avenue For Exploits in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. another common security vulnerability is unsecured application programming interfaces (apis). Apis provide a digital interface. In this article, we will. on our study. Interfaces That Provide An Avenue For Exploits.
From exploit-sec.blogspot.com
EXPLOIT ' SEC Interfaces That Provide An Avenue For Exploits Apis provide a digital interface. another common security vulnerability is unsecured application programming interfaces (apis). in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. attack. Interfaces That Provide An Avenue For Exploits.
From www.pinterest.com
Pin on Computer Interfaces That Provide An Avenue For Exploits In this article, we will. another common security vulnerability is unsecured application programming interfaces (apis). Apis provide a digital interface. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. in the context. Interfaces That Provide An Avenue For Exploits.
From slideplayer.com
Information Security Theory vs ppt video online download Interfaces That Provide An Avenue For Exploits Apis provide a digital interface. while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. another common security vulnerability is unsecured application programming interfaces (apis). attack vectors. Interfaces That Provide An Avenue For Exploits.
From pentest-tools.com
How to exploit the BlueKeep vulnerability with Metasploit Pentest Interfaces That Provide An Avenue For Exploits in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. Apis provide a digital. Interfaces That Provide An Avenue For Exploits.
From slideplayer.com
CET203 SOFTWARE DEVELOPMENT Session 3B Interfaces. ppt download Interfaces That Provide An Avenue For Exploits another common security vulnerability is unsecured application programming interfaces (apis). attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. while apis bring enormous benefits to the world of technology, they also introduce. Interfaces That Provide An Avenue For Exploits.
From slideplayer.com
1 Obfuscation and Tamperproofing Clark Thomborson 19 March ppt download Interfaces That Provide An Avenue For Exploits in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. Apis provide a digital. Interfaces That Provide An Avenue For Exploits.
From www.slideshare.net
LTE Architecture and interfaces Interfaces That Provide An Avenue For Exploits In this article, we will. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a. Interfaces That Provide An Avenue For Exploits.
From cedbxkck.blob.core.windows.net
What Is Interface Explain With Example at Craig Alexander blog Interfaces That Provide An Avenue For Exploits while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. another common security vulnerability is unsecured application programming interfaces (apis). attack vectors exploit system vulnerabilities, providing an. Interfaces That Provide An Avenue For Exploits.
From www.mdpi.com
Electronics Free FullText Analysis of Consumer IoT Device Interfaces That Provide An Avenue For Exploits In this article, we will. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. Apis provide a digital interface. while apis bring enormous benefits to the world of technology, they also introduce new avenues for exploitation and hacking. in the context of penetration testing, a pentester may use file inclusion exploits to assess. Interfaces That Provide An Avenue For Exploits.
From www.crowdstrike.com
How to enable exploit blocking in CrowdStrike Falcon Host Interfaces That Provide An Avenue For Exploits in the context of penetration testing, a pentester may use file inclusion exploits to assess the security of a target. on our study of 500 exploits, this paper surveys the different interfaces that are targeted in malware attacks and can. attack vectors exploit system vulnerabilities, providing an avenue for cybercriminals to access sensitive. Apis provide a digital. Interfaces That Provide An Avenue For Exploits.